Device Security And Visibility, Across Every Device
Secure your resources with real-time device queries before enforcing device trust using Beyond Identity's adaptive authentication rules.
Device Security And Visibility, Across Every Device
Secure your resources with real-time device queries before enforcing device trust using Beyond Identity's adaptive authentication rules.
By clicking “Submit” I agree to the Terms and Conditions.
Beyond Identity is trusted by top companies

Device access you control, with deep visibility on device security settings
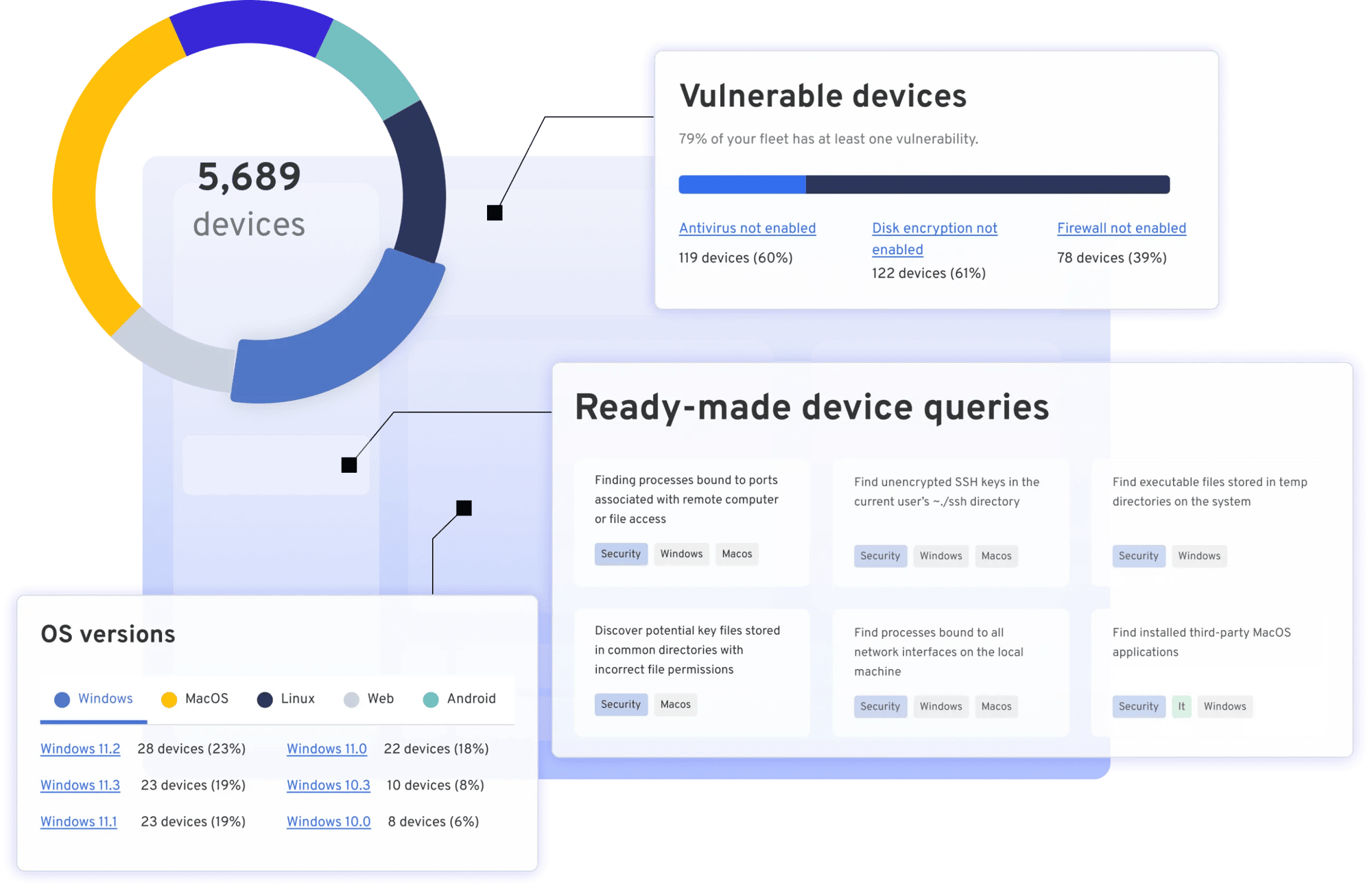
360 birds-eye view of your inventory
Streamline onboarding, offboarding, app requests, and policy with our easy-to-use workflows to keep your resources safe, while providing a seamless experience for your employees.
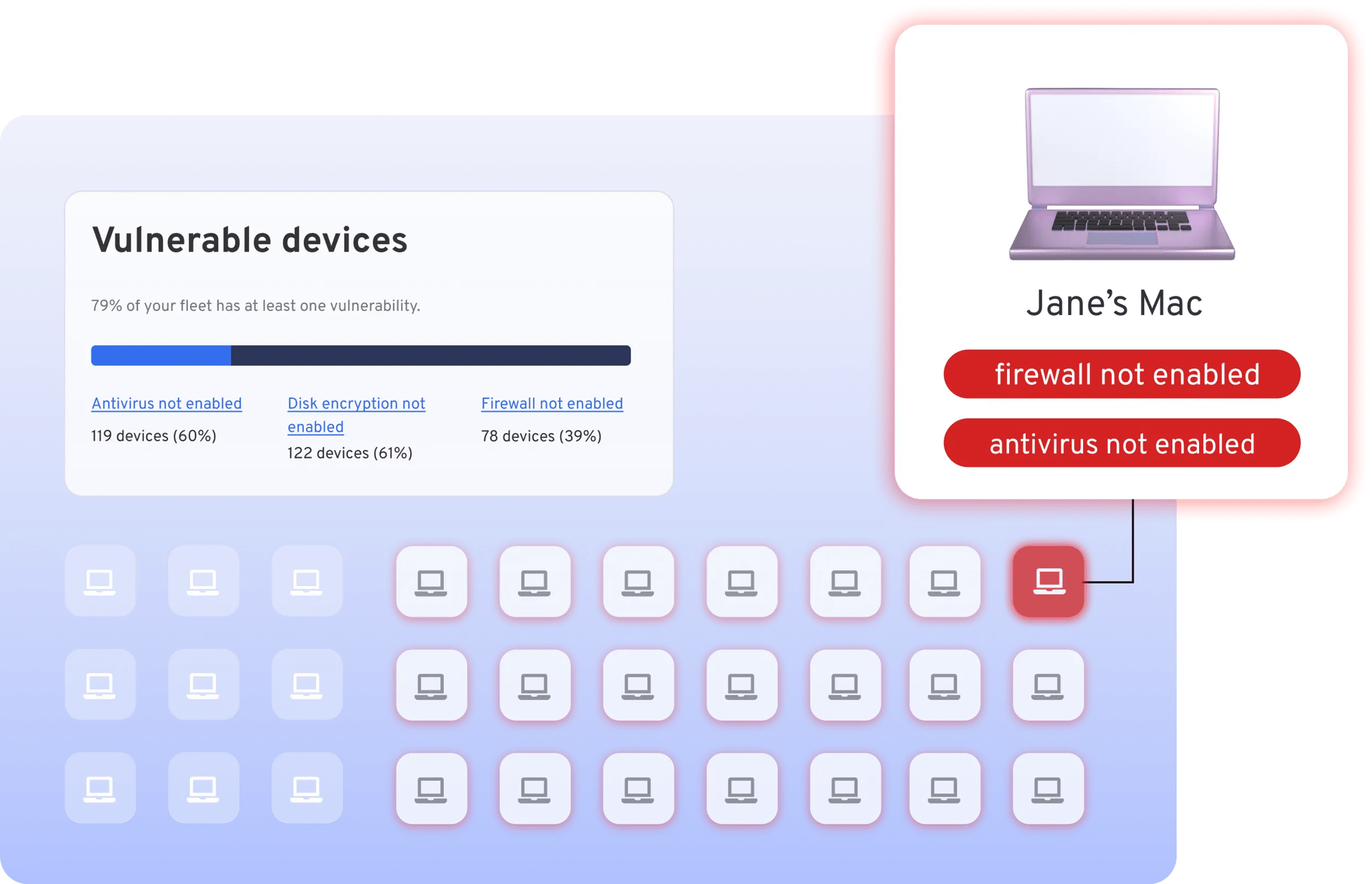
Manage risk and costs with 100% visibility into your fleet
Instantly identify weak links in your fleet, meet compliance requirements with single-click reports, and manage access with policies.
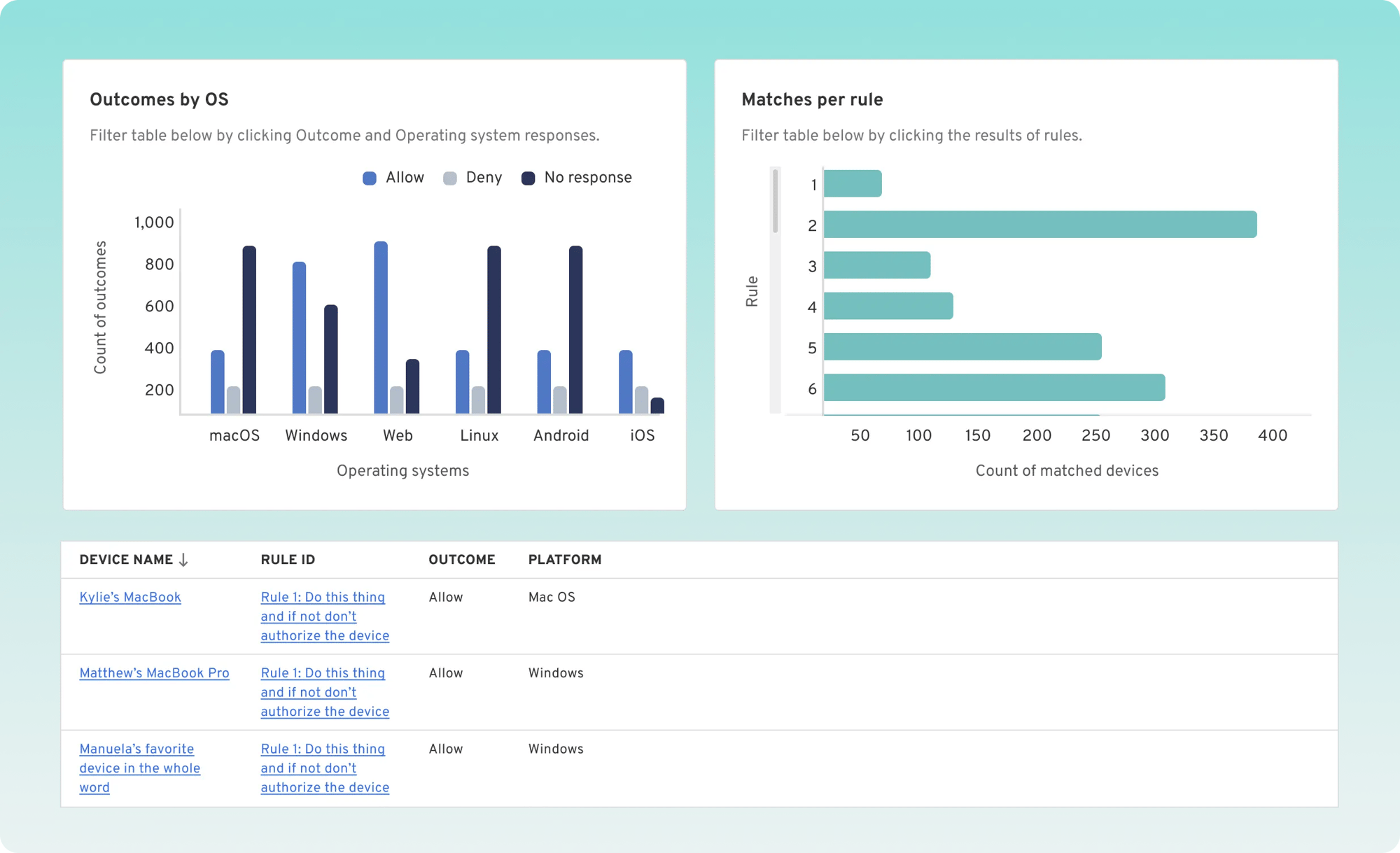
Test access controls before you deploy
Instantly identify weak links in your fleet, meet compliance requirements with single-click reports, and manage access with policies.
Protect access to your apps with passkeys
Eliminate your biggest threat vector, weak credentials, while delighting users with passwordless authentication.
Protect access to your apps with passkeys
Eliminate your biggest threat vector, weak credentials, while delighting users with passwordless authentication.